Password Hardening and Passphrases
Minimum Password Length
The length of a password can drastically increase or decrease the amount of time it could take for an attacker to crack a password hash that has been stolen or intercepted. Each additional character exponetially increases the amount of time and processing power required to successfully crack a password hash. At an absolute minimum you should strive to enforce a 15 character minimum password. We can take a look at some real world statistics below on lengths from Bitwarden:

Source Article Here
Why we recommend 15 character minimums
Windows Active Directory may try to use NTLMv1 authentication by default for older systems. Additionally, an attacked may be able to force an endpoint to use NTLMv1 authentication in a downgrade attack. NTLMv1 uses a Lanman hash that is stored in an insecure manner and easily cracked. Lanman hashes have a maximum password length of 14 characters, by forcing the password length to 15 we can effectively break NTLMv1 authentication and force the domain not to store Lanman hashes that can be easily cracked.
How in the world are we going to convince users to use such long passwords?
This is where passphrases come into play. The key difference is contained in the name itself - it is a phrase, not a word. Phrases are much eaiser for a user to remember while also maintaining a stronger sense of security by increasing the character count in a password.
A passphrase can be anything, it can even be about what you ate for lunch on Thursday afternoon, as long as you can remember the phrase.
Let's compare the two below:
The strength of a 9 character password
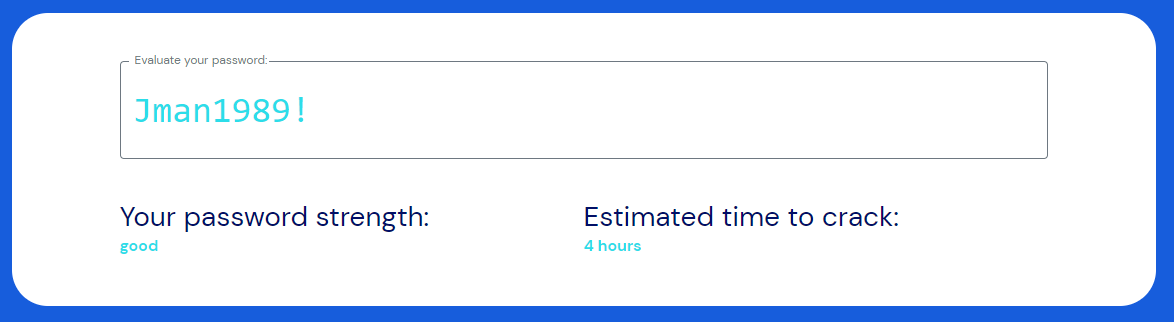
The strength of a passphrase
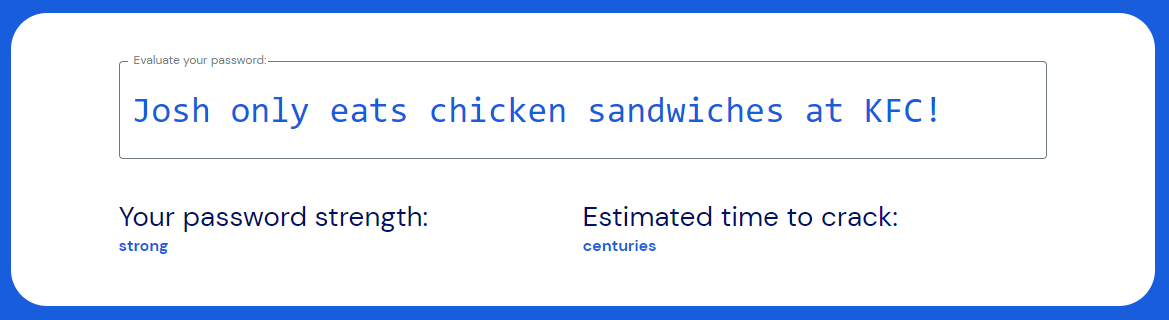
A simple passphrase brings our character count to 41 (spaces count as characters!), while also including a symbol to meet password strength requirements. This is a simple phrase that is rather easy to remember but nearly impossible to guess, and even more impossible to crack anytime this decade.
Encouraging users to utilize passphrases can be the difference between success and failure in rolling out longer minimum password lengths, as well as getting senior leadership on board with the necessary security changes.